In recent information leakage accidents, many people may have heard words such as "cyber attack surface (area with high possibility of being attacked by cyber)" and similar words. It's important to understand how cyberattacks occur and where the risks are in your organization. In this pandemic, this attack surface has expanded rapidly at an unprecedented speed. And unfortunately, today companies are unable to identify where and how complex they are likely to be attacked. As a result, digital and physical assets are left unattended, leaving room for cybercriminals to attack.
Fortunately, however, the best practices listed below are likely to improve the visibility of the attack surface. Visualization will allow us to take the necessary steps to minimize the attack surface and manage it properly.
What is an attack surface?
Simply put, an attack surface is a company's physical and digital assets that can be compromised to facilitate cyberattacks. Attackers have a wide range of purposes, including spreading ransomware, stealing data, forming botnets, downloading banking Trojan horses, and installing cryptocurrency mining malware, but ultimately aim to expand the target of attacks. .. In other words, the larger the attack target, the wider the attacker's target range.
Attack surfaces are broadly divided into two categories.
Digital attack surface
Includes networked hardware, software, and all other components.
Applications: Application vulnerabilities are common and attackers can be a valid entry point into critical information systems and data.

Code: Code compiled by a third party poses a great risk because it may contain malware and vulnerabilities.
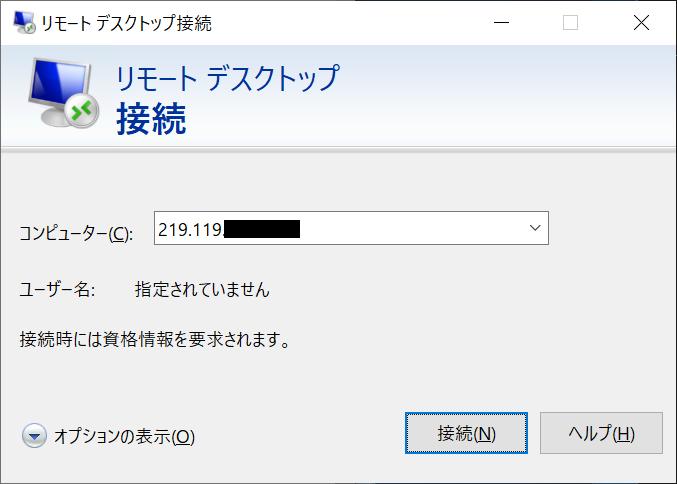
Ports: Attackers are hunting for open ports or services using specific ports. For example, TCP port 3389 used for RDP (Remote Desktop Protocol) can be targeted. These services can be abused if they are not properly configured or contain bugs.
Server: Can be the target of exploit-based vulnerability attacks and DDoS attacks.
Website: Elements such as code flaws and misconfigurations in the website are also included in the digital attack surface. Malicious code can be embedded, such as site tampering or formjacking.
Certificates: Many companies leave their certificates revoked and can be abused by attackers.
These do not cover all of the attack surfaces. The following is a summary of the survey conducted on FTSE30 companies in 2020 to show the rapid expansion of the digital attack surface.
Physical attack surface
Includes all terminals that an attacker can physically access.
Employees can also be said to be the main parties to the physical attack. That's because there is a risk of being guided by social engineering in the process of cyber attacks, including phishing scams and their variants. Some employees also do shadow IT, such as escaping corporate security controls and using unauthorized applications and devices. Unapproved tools often expose companies to new threats because they are not well protected.
Is the attack surface expanding?
Companies have been building IT infrastructure and digital assets for many years. However, pandemics have made significant investments to support remote work and maintain business in a dramatically changing business environment. Therefore, the attack surface is also expanding. The following is an example.
This trend will continue in the future. Experts say that many companies have reached a turning point in digitalization, where business practices will change permanently. These changes carry the following risks.
Moreover, the risk of attack surface expansion is not limited to the above. In fact, there are hundreds of attacker techniques, some of which are highly diffuse. For example, ESET discovered 71 billion attacks that broke RDP misconfiguration between January 2020 and June 2021.
To reduce the risk of attack surfaces
It's important to follow cybersecurity best practices when dealing with growing attack surfaces. The first step is to understand the scope and take measures to mitigate and manage it. Here are some hints.
The corporate IT environment is constantly changing. Specifically, it includes the spread of virtual machines and containers, microservices, employee hiring and leaving, and the introduction of new hardware and software. Therefore, in order to visualize and manage the state of the attack surface, a flexible and advanced tool that can make decisions based on real-time information is required. To mitigate the risk of attack surfaces, you should focus on "visibility and control" as well as other security measures.

![EVsmart blog Toyota's electric car "bZ4X" that makes you feel comfortable with electric cars and quick chargers / No% display of battery level [Editorial department] Popular articles Recent posts Category](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/9/752542064665dc2bd7addbc87a655694_0.jpeg)
![Lenovo's 8.8 inch one-handed tab "Legion Y700" full specs released! [Is the price in the 40,000 yen range?]](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/9/207e1be231154e91f34c85b4b1d2126c_0.jpeg)